
Real-Time |
|---|
| ||||||||||
|
 |
Version 6.1 |
|||||||||||||||||||||||||||||||||
|
|
The "basic" communication model assumes that endpoints can communicate directly, i.e. that all "entities", both clients (phones, softphones, PBX applications) and servers have "real" Internet IP Addresses. In this situation the Server is needed only to establish a call. Media data and (in case of SIP) in-call signaling requests are sent directly between the endpoints:
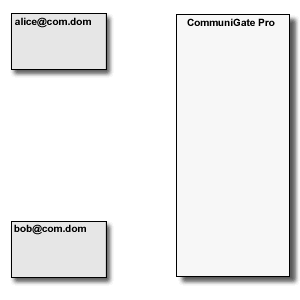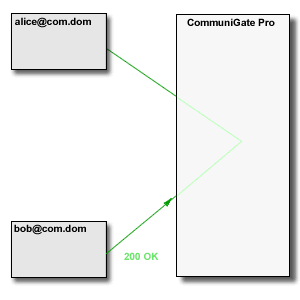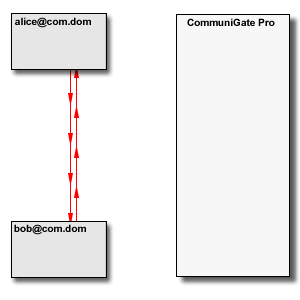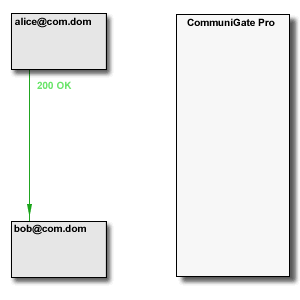
In the real life, many clients are located in remote LANs ("behind a NAT"), or in different LANs so they cannot communicate directly. CommuniGate Pro supports automatic "NAT traversal" for the standard-based Real-Time communications.
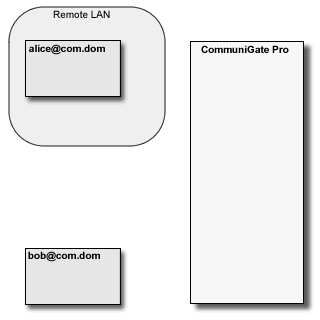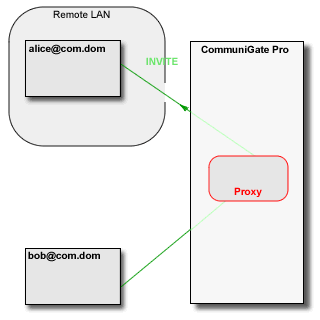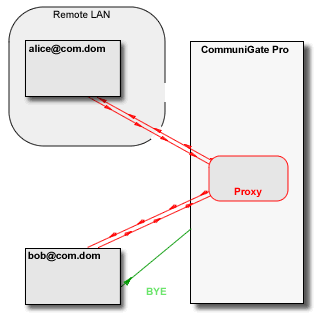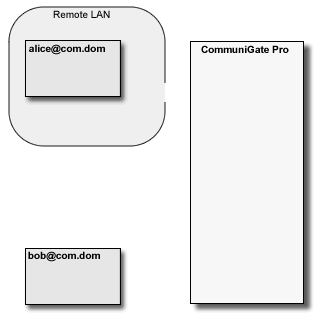
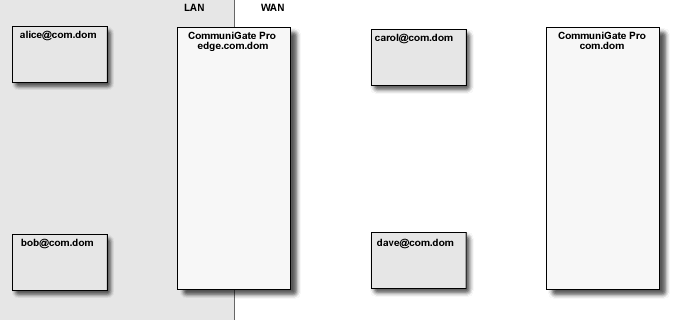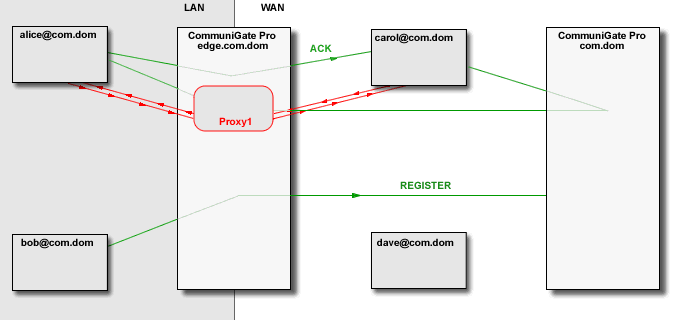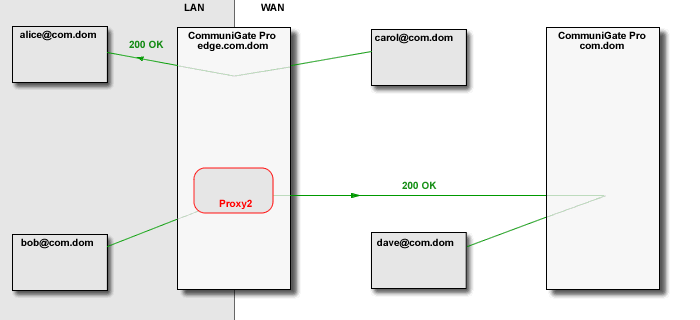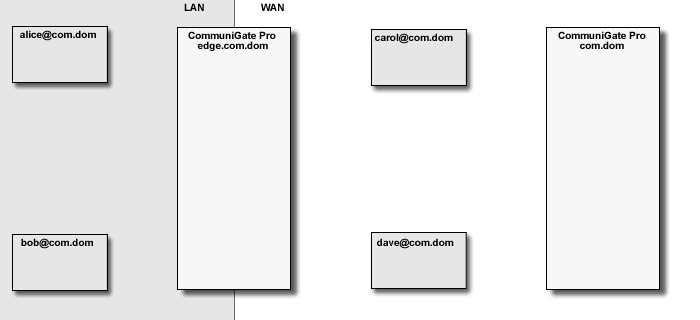
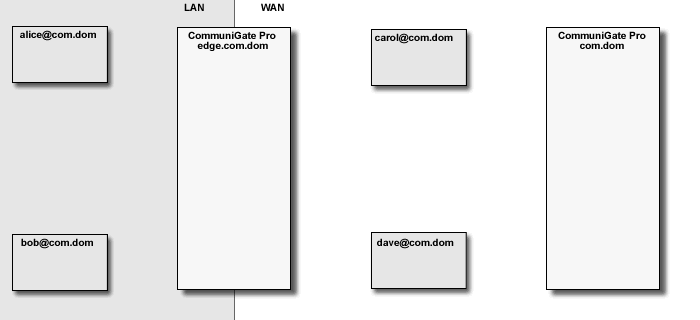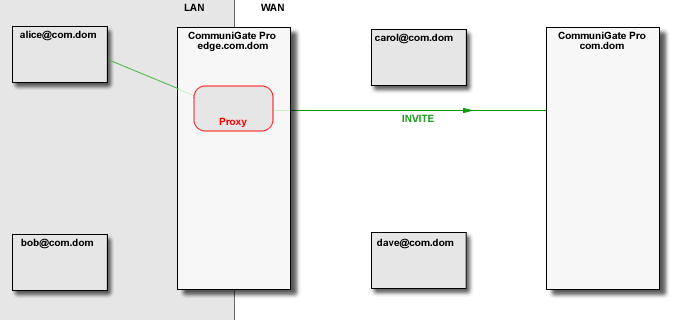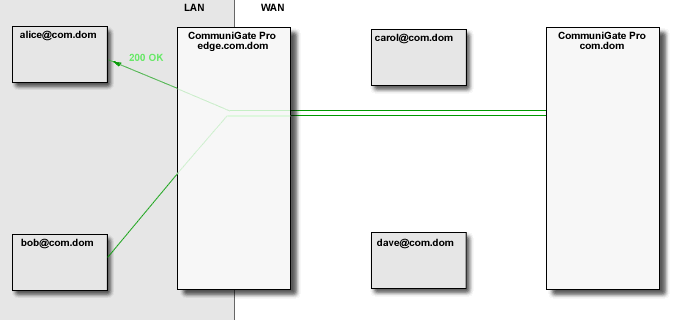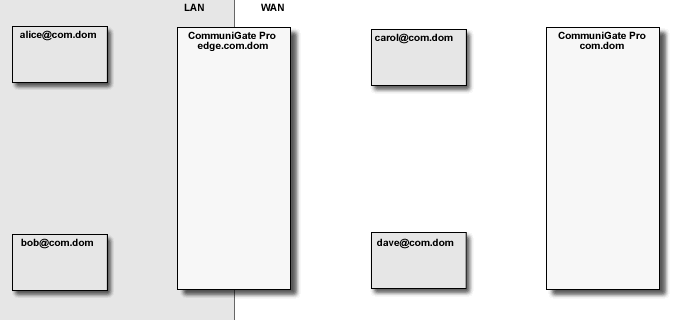
The CommuniGate Pro SIP and XIMSS Modules detect the session initiation requests that are sent from one side of NAT to the other side (a request from a LAN client to a party on the Internet/WAN and vice versa). In this case, the Server uses some local server port (or a set of ports depending on the media protocol(s) used) to build a media stream proxy. The Server then modifies the session initiation request to direct the traffic from both sides to that proxy.
The Media Proxy relays media data between the "LAN leg" and the "WAN leg" of the media connection: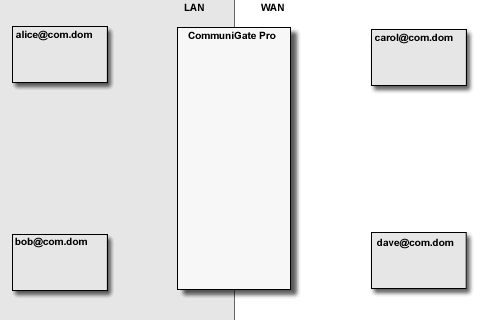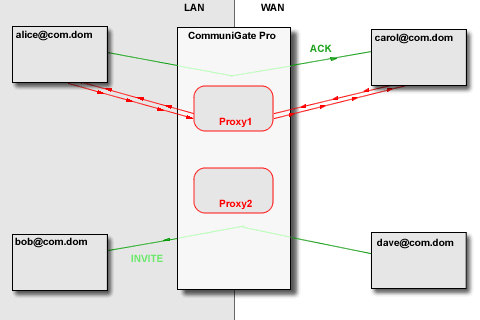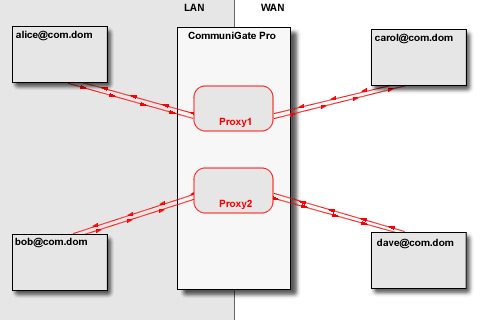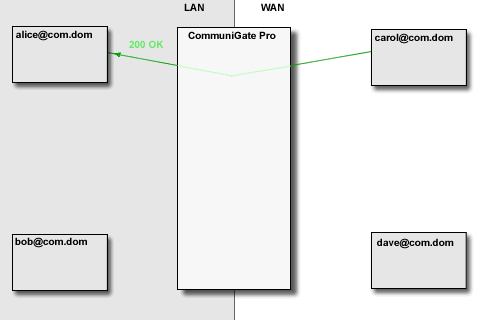
The CommuniGate Pro SIP and XIMSS Modules detect session update (SIP re-INVITE) and session close (SIP BYE) requests and update and remove the Media Proxies accordingly. The time-out mechanism is used to remove "abandoned" Media Proxies.
The CommuniGate Pro provides NAT proxy services for:Note: If you need the Media Proxy functionality, make sure that the LAN and NAT data is specified correctly on the LAN IPs and NAT WebAdmin settings pages.
Note: The Server automatically builds Media Proxies when it relays requests from IPv4 addresses to IPv6 addresses and vice versa.
The CommuniGate Pro SIP and XIMSS Modules also provide the "far-end" NAT traversal capabilities by detecting requests
coming from clients located behind remote Firewall/NATs.
The Modules add appropriate Record-Route and Path headers to these requests and they build
Media Proxies to relay traffic to and from those clients.
Note: modern SIP clients support various NAT traversal methods (STUN, etc.). Many of these implementations are quite buggy, so it is often more reliable to switch the client-side NAT traversal methods off, and rely on the CommuniGate Pro SIP Module far-end NAT traversal capabilities instead.
Note: due to the nature of the TCP protocol and the Firewall concept, it is not possible (in general) to open a TCP connection to a client behind a far-end NAT ("near-end" NAT configurations do not have this problem). This means that clients behind a far-end NAT cannot initiate TCP (T.120) sessions.
To solve this problem, you may want to:The CommuniGate Pro SIP Module can be used as an "Edge Service" or ALG ("Application Level Gateway"), providing NAT traversal functionality for users registered on other servers.
The CommuniGate Pro SIP Module detects "media loops", when a call placed from within LAN is proxied to WAN, and then proxied back to the same LAN. In this case the Media Proxies are removed, eliminating unnecessary overhead, and allowing SIP clients to communicate directly within one LAN, while proving registrar services outside that LAN.
The SIP module can detect much more complex loop cases, either avoiding Media Proxies altogether, or minimizing the number of Media Proxies used.
To detect clients located behind NATs, the Server needs to know which addresses are used on remote networks behind those NATs.
Use the WebAdmin Interface to specify the NATed Addresses.
Open the Network pages in the Settings realm, then open the NATed IPs page.
If a SIP client sends a request to CommuniGate Pro and the client own network address specified in the request headers is included into the NATed IP Addresses list, while the Server has received this request from a different network address, NOT included into the NATed IP Addresses list, the Server decides that this client is behind a NAT.
Some NAT servers make attempts to perform "SIP application gateway" functions, changing the
IP addresses specified in the relayed SIP requests.
Many of those NAT servers fail to perform
these gateway functions correctly, and CommuniGate Pro should treat clients connecting via those NAT servers using its
"far-end NAT traversal" functionality, but CommuniGate Pro cannot detect that this functionality is needed,
because the client IP addresses specified in their SIP requests are damaged.
You can specify the IP addresses of those broken NAT servers in the NAT Server IP Addresses field: all requests
coming from the specified Network Addresses are treated as requests from "NATed" clients:
You may need to relay requests to remote SIP servers (such as PSTN gateways) located behind a far-end NAT.
Since these servers do not issue SIP REGISTER requests to your CommuniGate Pro Server, there is no way to automatically detect
these far-end NAT traversal situations.
Include the public Network IP Addresses of these remote SIP servers into the NAT Server IP Addresses field to instruct
the CommuniGate Pro SIP Module to use far-end NAT traversal techniques when starting sessions with these SIP servers.
When clients connect to the CommuniGate Pro server from behind multi-homed NAT servers,
the client Signal (SIP, XIMSS) connections and media (RTP) streams can come from different IP Addresses.
When a client uses HTTP transactions to connect to WebUser or XIMSS session, the HTTP requests coming from
multi-homed NAT servers can come from different IP Addresses.
In thess situations clients can experience lack of media transfer or rejection of session requests caused by
a "wrong IP Address" problem.
To avoid this problem, two different IP Addresses are treated as the "same address" if both of them are included into the same IP Address range in the NAT Server IP Addresses list.
To send incoming calls to a SIP client behind a NAT, CommuniGate Pro keeps the "communication hole" between the client and Server open by periodically sending dummy packets to that client.
CommuniGate Pro supports various real-time communications. Most of those real-time protocols cannot be used via a NAT/Firewall, so CommuniGate Pro can act as "proxy" for those protocols.
When a client on the LAN tries to communicate with a remote system on the Internet (WAN),
CommuniGate Pro creates a Media Proxy - a communication port on its own system.
It forces the client to connect to that Media Proxy instead of the remote system media port.
The CommuniGate Pro Media Proxy communicates with the remote system itself,
relaying the data received from the LAN client to the remote system and vice versa.
A Media Proxy is created to serve entries (users) located behind remote NAT devices.
A Media Proxy is created to relay traffic between an IPv4 and IPv6 entries.
Note: some remote NAT systems are "multihomed". In this case, a signaling request
can come from one external IP Address of that system, while the media stream may come from a different IP Address.
CommuniGate Pro Media Proxies can support these NAT systems if all their external IP Addresses are included
into a single IP Address range, and if this IP Address range is included into the NAT Systems list.